Back in May, I discovered an issue with the Netcraft anti-phishing toolbar extension for Firefox that resulted in security information from one website would be inherited by any subsequently website being loaded over IPv6.
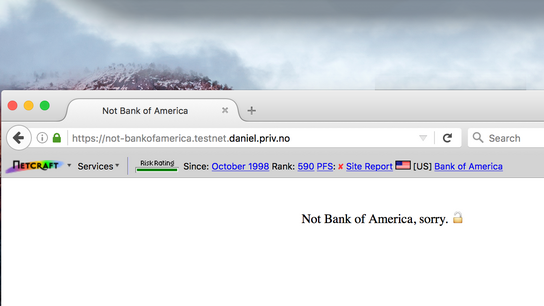
The feature image above shows the site information and trust rating score from Bank of America inherited by a test page that was loaded after visiting Bank of America’s website. Any IPv6 enabled website would inherit any previously loaded IPv4-only website’s information. Note that the test page had PFS enabled, but inherited Bank of America’s lesser capabilities.
A genuinely fraudulent URL would still have been blocked, as the main blocking functionality is handled separately from the function that displays this information. However, the advisory information meant to reassure users that they’re visiting the website they think they are can easily be replicated by another site not yet in the toolbar’s blocklist.
This issue demonstrated two problems with how the toolbar works:
- It failed to clear out the previous website’s security information when navigating away from it.
- It failed to retrieve information for IPv6 websites.
After notifying Netcraft about the issue, they released the Netcraft toolbar version 1.10.3 on . In this version, IPv6 resolution was disabled on the client-side resulting in information from the IPv4 server being displayed for IPv4/IPv6 dual-stack web servers. The Netcraft service itself is hosted in an environment without IPv6 connectivity, so the service can’t yet be made IPv6 aware.
There’s no guarantee that IPv4 and IPv6 would be handled by the same or even similarly configured web server. One server could be compromised while the other would serve legitimate content. The security information can thus still be incorrect for IPv6 websites.
The root cause of the issue was a misreferenced variable when loading the string “[No information available string]” that resulted in one of the more amusing JavaScript error messages I’ve seen in a while: “daddy isn’t defined”. The toolbar is obviously having some existential crisis regarding of if its parents here. When the daddy reference failed to resolve, the previously loaded website’s information would remain on the toolbar. In the updated version of the toolbar, the message “[No information available]” will be correctly displayed for IPv6-only websites.
Information is unavailable for IPv6 websites as Netcraft’s own servers aren’t yet IPv6 capable. This greatly limits the toolbar’s usefulness when visiting any of the web’s most popular websites—including Facebook, Google—as they’re accessible over both IPv4 and IPv6 now.
Phishing sites is detected using URLs so the main phishing protection feature would still be working on IPv6 websites even though the toolbar would display the wrong site information on the toolbar itself. The information on the toolbar is meant to reassure the user that they’ve indeed arrived on the right website.
The security information in the Netcraft toolbar isn’t to be trusted in any case. For every website it requests security information about, it retrieves it over an unencrypted HTTP connection rather than an encrypted HTTPS connection. The full URL of HTTP pages and the domain of HTTPS pages are included in the unencrypted connection to check whether the page is fraudulent.
The plain-text JSON response message the toolbar gets back from Netcraft could be intercepted and altered to show that everything is as it should be by a attacker-in-the-middle attacker. Alternatively, the response could just be blocked resulting in the toolbar displaying a response timeout message rather than a fraud warning.
The Netcraft toolbar for Firefox has 12 000 weekly active users and sees around 500 new downloads every week, according to the Firefox Add-on portal. Netcraft’s Chrome extension has 25 500 weekly users, according to the Chrome Web Store.
The Netcraft toolbar was first release back in 2005, and was innovative for its time. It was one of the web’s first anti-phishing countermeasures in a time when web browsers didn’t come with built-in malware and fraud protection services. However, just within two years of the toolbar’s release, built-in phishing protection services had appeared in Firefox, Internet Explorer, and Opera. Some possibly built on data licensed from Netcraft. The toolbar’s relevance have kept dwindling into oblivion since then. I’ve installed it on two computers in my household and the toolbar often just displays the message “[Rate limit hit]”, which isn’t very trust-inspiring.
The design of the toolbar looks virtually indistinguishable from how it appeared when it first launched in 2005. It has gained a few new bells and whistles, but functionally as well as visually it’s very much a product of the browser toolbar era.