Lenovo laptop customers with the Lenovo Vantage app for Windows 10 (preinstalled by default) are being prompted to enable a new feature called Lenovo Wi-Fi Security. Lenovo claims the feature will help protect its customers against “malicious Wi-Fi networks”. But what does the feature do? and should you bother enabling it?
Lenovo Wi-Fi Security promises that it will, somehow, “help protect you from connecting to malicious Wi-Fi networks” and “reduce the risk of having your computer and data exposed to attackers”.
However, there are very few details available about how Lenovo Wi-Fi Security works and what it does once its enabled. It’s also hard to get any concrete details about the feature out of Lenovo or Coronet Cyber Security; an Israeli company that provides the infrastructure that powers Lenovo Wi-Fi Security.
Lenovo Wi-Fi Security appears to be a branded distribution of Coronet SecureConnect; a product of which there’s no specific information available on the web. Coronet hasn’t published much details about how any of their services work, but I’ve been able to dig up some hints here and there from historical product pages and news snippets.
So, what does Lenovo Wi-Fi Security protect against?
It’s unclear exactly what capabilities Coronet SecureConnect has and which have been incorporated into Lenovo Wi-Fi Security as there’s no documentation available about either. I’ve collected some of the most specific statements I’ve been able to find regarding Coronet’s claimed capabilities:
Coronet can detect and evade unsafe wireless connections over both Wi-Fi and Cellular networks. It can also rate and keep record of popular network scores […].
Network-in-the-middle attacks (evil twin, PNL honeypots, compromised captive portals). Traffic interception, attempt to steal encryption keys and certificates.
Coronet’s SecureCloud, the platform that offers end to end outside the perimeter security, confirms that it’s the first company to offer protection against KRACK.
These statements are all made about Coronet SecureCloud product and not their SecureConnect product. I’ve asked Coronet and Lenovo multiple times to provide more specific details about Lenovo Wi-Fi Security, but I haven’t received a reply from either companies.
Let’s put it to the test
I’ve set up a few different test networks that should seem suspicious, including one with WPAD/DHCP-PAC (proxy auto-configuration), a transparent proxy, and poisoned DNS responses. I even walked about Oslo city center and connected to more than 50 open Wi-Fi access points. All of these networks were cleared by Lenovo Wi-Fi Security as “compliant” with a green rating.
I only managed to trigger a warning from Lenovo Wi-Fi Security after connecting to a Wi-Fi access point that relayed all traffic through a Tor exit node in Russia using my InvizBox.
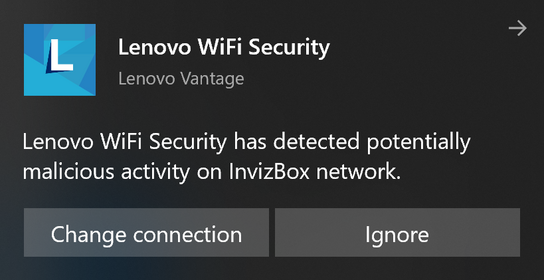
“Lenovo Wi-Fi Security has detected potentially malicious activity on InvizBoz network.”
At least one of the Wi-Fi access points I connected to is known not have been patched against the KRACK Attack vulnerabilities. I also doubt that all the networks and devices I connected to in the Oslo city center would have been patched and updated.
I’m frankly surprised more of my attempts weren’t detected as malicious. I thought a transparent proxy would trigger warnings for sure. It’s also notable that you only get one notification from the app informing you about a potential malicious network. You can’t get any more information about the potential risk than the rating (green, yellow, or red).
On one of my household’s three Lenovo laptops, Lenovo Wi-Fi Security will go into an infinite crash loop every minute or so when enabled.
Privacy and location data
Part of the information that Lenovo Wi-Fi Security collects about wireless networks is the same information used to location-triangulate devices. You’re prompted to grant the Lenovo Vantage app access to your device’s location through the Windows.Devices.Geolocation service when you enable Lenovo Wi-Fi Security. Read this article for an introduction to this broader topic.
Lenovo’s Product Privacy Statement doesn’t mention Lenovo Wi-Fi Security, Coronet Cyber Security, or the collection of location data. I contacted Lenovo’s dedicated privacy contact and got the following statement:
Coronet collects anonymized information about the wifi access points in the surroundings of the user device and communicates part of this information to the servers of Coronet Cyber Security. This information is used to generate aggregated knowledge about the wifi networks and is used to allow certain user protection capabilities provided by Coronet.
Email correspondence, , Lenovo Privacy Program
The following statement comes form Coronet Cyber Security’s own Privacy Policy. Importantly, this policy does not apply to Lenovo Wi-Fi Security as Lenovo customers are never presented with the policy and are never told about the service’s use of Coronet’s infrastructure.
[Coronet] also collect technical information transmitted by your device, including certain software and hardware information (e.g. your carrier, your operating system, your approximate location, etc.) and information regarding the behavior and usage of networks around and by your device to provide you and the License Holder with analysis, in respect to potential threats. Such information may include specific network configurations, but will not include any information that was transmitted through the networks (e.g. SMS; online browsing; phone calls, etc.) ” “[…]
We will not share your e-mail address or any other personally identifiable information with online advertisers and advertising networks, without your explicit consent.
Marketing materials from Coronet shows the location of end-user devices plotted on a map, but this is probably related to Coronet’s other service offerings for enterprise customers. However, it does confirm and demonstrate their capabilities to track the location of customers. It’s worrying that Lenovo haven’t included more detailed information about their partnership with Coronet Cyber Security in their privacy policy, and that they don’t talk about or promote the service except for the notification prompts they send to Lenovo Vantage app users.
Conclusions
I don’t know what to make out of Lenovo Wi-Fi Security. I can see the value proposition, but the service doesn’t seem to deliver on it. It doesn’t provide enough information to genuinely help people make good decisions about Wi-Fi network security. It also doesn’t block you from connecting to malicious or suspicious networks. I expected it to abort the connection and prompt me for a confirmation before establishing the connection. All you get is one easily missed notification.
I’m also surprised by the lack of transparency in how the service works and its implications on your privacy. Do you want to send your device location data to an Israeli company?
The short and long of it’s that you should never connect to a public Wi-Fi access point. Lenovo Wi-Fi Security can only leave you with the false sense of security and make you trust networks you shouldn’t use.
If you absolutely must connect to a public Wi-Fi access point, then the only thing that can offer you some level of protection is a Virtual Private Network (VPN) provider. Assuming, of course, that you can trust your VPN provider and you don’t end up putting them in a position where your VPN can intercept your traffic more easily than a compromised or malicious Wi-Fi network.
